The difficulties of installing an SSL certificate on a ZyXEL ZyWall USG 300 firewall (if even possible!)
Having spent some time trying to install an SSL certificate from a trusted certification authority on this product, I felt I should share my findings as they might save someone else the headaches and time I had to spend on this.
For reference I used a ZyXEL ZyWall USG 300 with Firmware version: 2.20(AOE.6) / 1.11 / 2011-10-05 11:51:34
I assume this information is the same for pretty much all versions of ZyWall products, but I can not confirm this from own testing as I only had access to one edition.
About Intermediate SSL certificates
All certificates today that want to enjoy the WebTrust approval must use intermediate issuing certificate authorities, this means that a root certificate is no longer allowed to directly issue server certificates for customers. This makes good sense security wise, as it is much harder for a hacker to gain access over the root certificate when it is not online and in case of a compromise, it should be sufficient to close the intermediate, without having to “remove/uninstall” the root from every client in the world.
So most professional products around that uses SSL certificates must be able to install both a server certificate and the intermediate issuing certificate, because the client only knows the root certificate, it needs the server to give it both.
Installing SSL certificates on ZyXEL ZyWall USG 300 (the good part)
Go into Configuration -> Object -> Certificate
Some things to have in mind when installing certificates on a ZyWall: The filename will also be the name of the certificate in the console (can be renamed after installation), all names MUST be unique and not quite short, do not install a filename that exists, rename first. Do not have spaces in the filename. I used files with .cer, .pem, .pfx without problems. I used PEM and PKCS12 formatted certificates.
Begin with installing the Trusted Certificates, look at the top tab named “Trusted Certificates” click there 🙂
In the bottom click on the button “Import” and select your Root CA certificate in pretty much any format.
Also install the Intermediate CA certificate for your product under Trusted Certificates!
Only when this is done should you attempt to enable the certificate for any service!
Now install the certificate, either by doing a CSR and then importing the response from your CA. Or import a PKCS#12 formatted pfx file with ONLY the server certificate and server key! If it also contains root and intermediate certificates (which is normal) it will not install correctly and will crash any service you enable it for.
You can confirm your server certificate is installed correctly by looking at the certificates “Subject” in the ZyWall console, if it is not the server name, but instead the name of the Root or Intermediate certificate you have a problem.
When you enable a service with this newly installed certificate, do remember that the administration interface is the webservice that also runs SSL VPN, and so on, so if it does not work, you also loose access to the web interface and you will be forced to use SSH to set the certificate back to default (which is also why you should not remove the default certificate). If you want to play safe, try the new SSL certificate on the SSH service first, but do make absolutely 100% sure it works before putting it on BOTH SSH and the webservice – obvious reasons.
Installing the intermediate SSL certificate on a ZyWall USG 300 from Zyxel (the not so good part)
This is where the fun comes in, I tried everything from order of certificates in PKCS12 and PEM formatted files, none of them allow the server certificate and intermediate certificate to be installed together (this is usually a simple fix for some NAS boxes, apache and OpenSSL based systems, when a SSL Chain File configuration option is missing).
It does not help that you installed the intermediate into trusted certificates, well it does without it, the ZyWall would not trust its own server certificate, since it is ALSO unable to find the intermediate certificate it self. But no it does not deliver it to clients.
Having tried all ways I could think of I ended up spending some time talking to Zyxel support and got a convering message, I was told I could forget it, it is not possible to get intermediate SSL certificates working on the ZyWall product, and they are aware of this. This must have been a problem they have known about for more than a year, since it is longer since all certificate authorities started going away from issuing certificates without intermediates.
How a product with a technology called “SSL Application” and “SSL VPN” can not even support the installation of a SSL certificate from a trusted authority is beyond me (Sorry ZyXEL if you are reading, but it is not ok!).
Errors because of this
When you have not installed the intermediate certificate, you might not even discover this at first, because browsers like Internet Explorer automatically finds the missing certificate and can then verify the SSL certificate. But not all browsers do so some will fail, you might think this is a bad certificate you bought and that is why, but this might just be the missing intermediate, if in doubt have a look at my SSL Server Test tool (FREE) here at www.ssltest.net it will let you know if something is missing.
But even if Internet Explorer finds the missing certificate, you still get a Security Warning when using VPN SSL because Java does not automatically find it, so it will prompt the user saying the web site certificate can not be verified, if you want to continue and if you want to always trust content from this publisher.
What to do ?
I was told next firmware upgrade at version 3.0 will have support for Intermediate SSL certificates (I think they should say the product will only support SSL at this version, as currently they only support self-signed certificates!). So time to look for when the firmware comes – as of yet it is not ready. If you haven’t bought one yet, don’t at least until the new firmware is ready!
A new firmware supporting intermediates has been released.
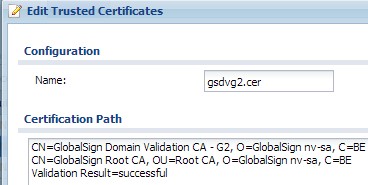 You can find the ZyXEL firmwares on their website (sorry but they break the link without a redirect, so you will have to find it your self). Funny part here is that their website uses intermediate certificate – so it is not like they do not know they need them.
You can find the ZyXEL firmwares on their website (sorry but they break the link without a redirect, so you will have to find it your self). Funny part here is that their website uses intermediate certificate – so it is not like they do not know they need them.
A quick how to install with intermediates.
I have successfully installed certificates by importing the certificate and key in a PKCS#12/.pfx file, but it must not contain the chain/intermediate certificates in the .pfx file. The Intermediate and root certificates are to be imported seperately on the trusted certificates tab only.
After this, the chain will be validated on the main certificate you imported. And it can be used and will present intermediates and root certificates when talking to the “world”.
New Problems with SHA-2 ? – updated august 2014.
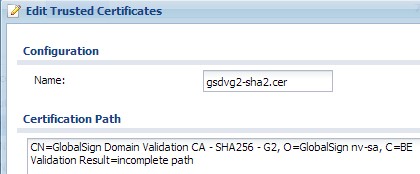 I have had problems getting the chain to work, with a SHA-2 certificate. The chain could not be validated for the SHA-2 intermediate certificate and therefore also failed for the SHA-2 server certificate. The SHA-1 intermediate from the same root, did not fail.
I have had problems getting the chain to work, with a SHA-2 certificate. The chain could not be validated for the SHA-2 intermediate certificate and therefore also failed for the SHA-2 server certificate. The SHA-1 intermediate from the same root, did not fail.
In the end, I reissued the server certificate using SHA-1 instead of SHA-2 (SHA256), and it worked fine then. Not sure if this is a one off problem, or for all SHA-2 certificates. This was on a Zyxel USG 300, with firmware 3.00(AQE.4) and I did not have the option of updating the firmware to see if the problem still exist in newer versions.
Great Info..! However it works like a charm on a Cisco ASA Firewall 🙂
Intermediate Certificates work perfectly on USG 300 with firmware 3.00(AQE.0) applied.
Thanks man! Nice work.
I can confirm that SHA-2 does not work. I had same issue with intermediate certificate. SHA-1 works fine.
USG 110 with firmware V4.10(AAPH.1).
Thanks for your notes on working through this issue Sole.
Hi,
I have tested on a USG20 firmware 3.30 BDR.7 and have no issues with RSA2 or intermediate certififcates. (though i have to import root and intermediate certificates manually as you also report..)
Thomas