How to configure Exchange 2007 and ISA with FBA and NTLM, without loosing ActiveSync on the way
Basicly we are here, because we want to use Forms Based Authentication (FBA) for our Outlook Web Access (OWA) users in Exchange 2007, while still using NTLM/Kerberos authentication for Outlook Anywhere (OA), wich in turn means less entering of the users password, while still not killing our ActiveSync clients since they only run Basic authentication.
Confused? let me try and make it easier.
- We prefer FBA for OWA, it is just more nice for the user to get a webpage to login to their OWA.
- We prefer NTLM for OA, it gives less password prompts and well it sounds safer than basic authentication
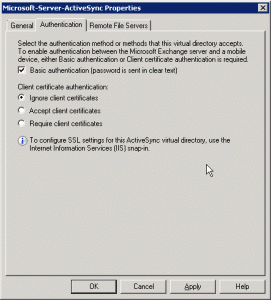
- We still want ActiveSync with Basic, but it fails if we use NTLM on our connection as well so we need to seperate them

What is the solution? Well its rather simple, we configure our services to use the authentication as we prefer, but we need to do some configuring of public DNS, Public IP’s and ISA to get all 3 authentication schemes to work at the same time. Basicly NTLM and Forms Based Authentication just does not mix. If you use FBA on a listener in ISA it will always fallback to Basic authentication if the client does not support FBA. It is not possible to use NTLM and FBA on the same ISA 2006 listener.
I have added screenshots of the important bits of the configuration in the bottom, and You should have all the required info to get it working, but You will need some basic knowledge of how to setup up Exchange 2007, ISA 2006 with Exchange 2007, etc.
We will split up the connections using two public fully qualified domain names (FQDN’s), since we are using one address for OWA and we need the AutoDiscover address as well, why not stay with thoose two addresses? In my example I will use the following assumption on my server and its data.
- I have 1 Exchange 2007 server, with all roles installed on it (if Windows 2008, dont forget the IPv6/RPC proxy bug). It could just as well be multiple Exchange servers, but slight changes would be needed, extra internal names in the SSL, configuration to load balance multiple CAS servers, etc.
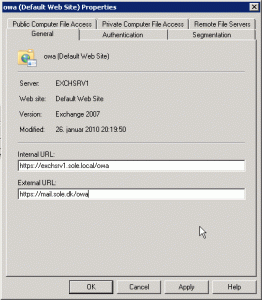
- I have a SAN certificate with the following names included: owa.sole.dk, autodiscover.sole.dk, exchsrv1.sole.local (In my case I use a GlobalSign DomainSSL SAN from FairSSL)
- All local clients access the Exchange server directly, all external clients go thru my ISA 2006 server
- Externally i have DNS setup for owa.sole.dk pointing at public IPv4#1
- And external DNS setup for autodiscover.sole.dk pointing at public IPv4#2
- Internally the address exchsrv1.sole.local points at the Exchange servers internal IPv4
- So I have 2 public IP‘s pointing at the ISA 2006 server and 1 internal IP on the Exchange 2007 server
With the configuration of public DNS, SSL certificates and routing and stuff out of the way, lets look at my configuration on Exchange 2007 and ISA 2006.
Exchange 2007
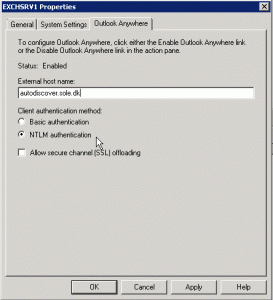
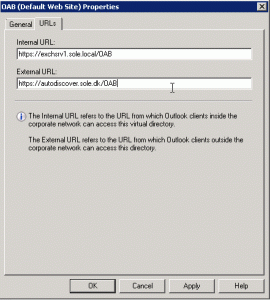
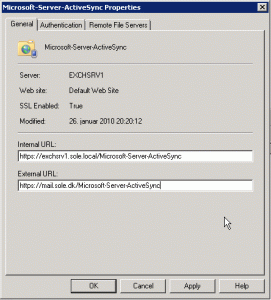
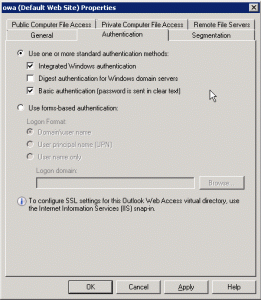
In summary I will configure my Exchange 2007 services with FBA/Basic on owa.sole.dk and NTLM on autodiscover.sole.dk, so I use the table below to configure the externalUrl and internalUrl and authentication method for each of the services.
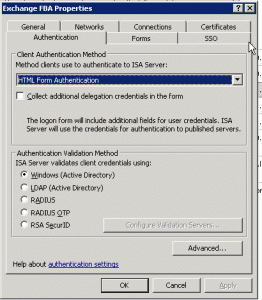
ISA Rule #1 “Outlook Web Access”
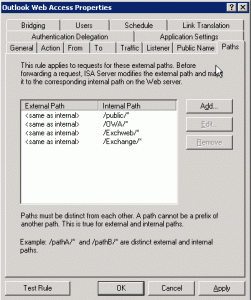
- Outlook Web Access – Basic / Forms Based Authentication – FQDN owa.sole.dk/IPv4 Listener #1 “FBA”
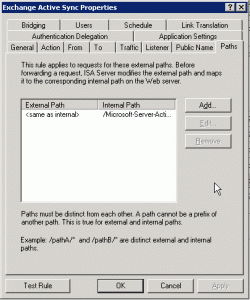
ISA Rule #2 “ActiveSync”
- ActiveSync – Basic Authentication – FQDN owa.sole.dk/IPv4 Listener #1 “FBA”
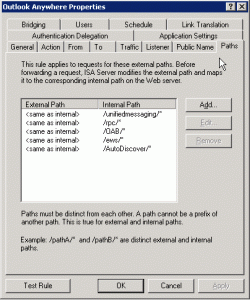
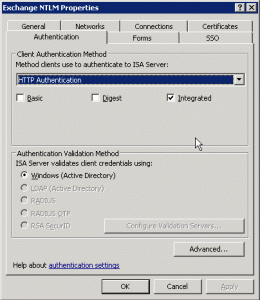
ISA Rule #3 “Outlook Anywhere”
- Outlook Anywhere – NTLM Authentication – FQDN autodiscover.sole.dk/IPv4 Listener #2 “NTLM”
- AutoDiscover – NTLM Authentication – FQDN autodiscover.sole.dk/IPv4 Listener #2 “NTLM”
- Offline Address Book – NTLM Authentication – FQDN autodiscover.sole.dk/IPv4 Listener #2 “NTLM”
- Exchange Web Services – NTLM Authentication – FQDN autodiscover.sole.dk/IPv4 Listener #2 “NTLM”
The following image shows the rules.

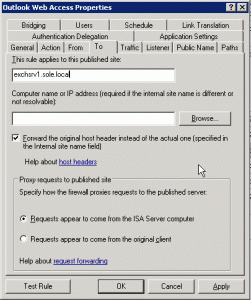
For all services I set the internalUrl to the relevant url with https://exchsrv1.sole.dk/…
ISA 2006
As You might have guessed by the above, I am going to configure my ISA 2006 with 3 rules using 2 listener’s/IP’s/FQDN’s
Rule #1+2
Wizard: Outlook Web Access & ActiveSync
IP: IPv4#1 with DNS: owa.sole.dk
Listener Authentication: Forms Based Authentication (Automatic failover to Basic authentication)
SSL Certificate: My GlobalSign DomainSSL SAN certificate (Dont forget the special Exchange intermediate from GlobalSign)
Rule #3
Wizard: Outlook Anywhere
IP: IPv4#2 with DNS: autodiscover.sole.dk
Listener Authentication: NTLM (HTTP Integrated Authentication with Kerberos constrained delegation – do not forget to set delegation in AD on the properties of the firewall/exchangeserver)
SSL Certificate: Still my same as above GlobalSign DomainSSL SAN certificate
Testing it works
To test that it all works and find any mistakes/errors I primarily use www.testexchangeconnectivity.com, www.ssltest.net, Internet Explorer, Outlook 2007 and a mobile device.
- SSL tester to ensure the certificate is installed correctly.
- I perform both ActiveSync, Autodiscover and Outlook Anywhere tests, with www.testexchangeconnectivity.com that should be working before I try with clients.
- For testing AutoDiscover and all the URLs the client gets from AutoDiscover, I use the Outlook client, by holding down CTRL and right clicking the Outlook Icon in the quickbar? (right corner where the clock is) and select Test Automatic Configuration.. and deselect all but Autodiscover. The XML recieved is gold worth in telling you if you forgot to set a service url.
- I also try and access the services with Internet Explorer to see if authentication works or if it keeps prompting, a mismatch is there. ie. https://autodiscover.sole.dk/Autodiscover/Autodiscover.xml (should authenticate and give an invalid request 600)
Exchange2007 Screenshots
Here You can find screen shots of my configuration, You still need to configure more than this thru the Management Shell, ie. EWS (hint Set/Get-WebServicesVirtualDirectory). Click on the image to get full size.
ISA Screenshots
Again there is more configuration to be done than below screenshots, but it should show you the important parts that You might be in doubt about. Click on the image to get full size.
Does it work?
It works for me, I get no errors in any testing tools, the clients use the authentication intended. But by all means put a comment here if You made it work or You did not make it work. Also any typos, errors or information that is obvious for me but maybe not for others, feel free to comment them here.
Things to remember that might trick you up:
- Set delegation for the computer AD objects to allow kerberos constrained authentication delegation.
- In rules set the name of the internal servername to the primary common name in the SSL if passing it on with SSL, then set the actual IP to forward to so it ignores this name i.e. www.sole.dk
- If in doubt about your delegation of authentication working, change temporarily to do not authenticate but allow client to authenticate directly, this will let you test where to fix your problem
- You need two listeners and two public IP’s for this setup. One with NTLM and one with FBA authentication. If you only have one IP, forget all this and just use FBA/Basic for all.
- Remember to set Exchange server to use the same authentication schemes as defined in ISA 2006
You may use this article as a reference, link to it and do as You please with it, as long as You give me some credit for the original content 🙂
Enjoy!
Just a small reminder.
When using ISA server to publish the Exchange 2007 CAS server(s), do not use Forms Based Authentication on the web services of the CAS server, instead use Basic/NTLM as needed and if wanted use Forms Based Authentication on the ISA server.
[…] and NTLM with my other services. You can see more information about this from my previous blogs here. Some people argue for and against having internal server names in the certificate, but I figure if […]
[…] Update: I have written a more comprehensive and slightly more technical blog about how to do this, take a look at How to configure Exchange 2007 and ISA with FBA and NTLM, without loosing ActiveSync on the way […]
Hey Sole,
It has been a few years since you have published this article, but I just wanted to say thank you, since it helped us configure Outlook Anywhere with NTLM auth. using KCD, together with FBA for OWA on Exchange 2010 SP3 and TMG.
I am glad it could help and thank you for letting me know.