How to disable administrative shares on workstations thru Group Policy and avoid spending time on pesty virus infections
 Large companies sometimes have problems with a virus that realy loves administrative shares on other workstations (i.e. c$ and admin$), it will try and break into theese to spread it self directly. The easy option ofcourse being kill the virus or even better harden administrative users and not use administrator rights for normal users! But untill that is an easy, non-political and not so time consuming task, why not disable the administrative shares on the workstations alltogether?
Large companies sometimes have problems with a virus that realy loves administrative shares on other workstations (i.e. c$ and admin$), it will try and break into theese to spread it self directly. The easy option ofcourse being kill the virus or even better harden administrative users and not use administrator rights for normal users! But untill that is an easy, non-political and not so time consuming task, why not disable the administrative shares on the workstations alltogether?
Seems like a perfect thing to do with Group Policy, unfortunately the setting is non-existing default in Group Policies, so by finding the registry key we need to change, a small custom administrative template will do the trick. This could also be used for other registry changes needed with group policy.
We might also want the option to easily enable the administrative shares later, might be used by applications, services, automated installations, etc. Heres is how to do it quick and easy.
Create a file named adminshares.adm with the content from below, under C:\windows\inf on the server You edit your GPO’s with.
CLASS MACHINE CATEGORY !!category1 CATEGORY !!category2 POLICY !!policyname EXPLAIN !!DefaultSharesExplain KEYNAME "System\CurrentControlSet\Services\LanManServer\Parameters\" VALUENAME "AutoShareWks" VALUEON NUMERIC 1 VALUEOFF NUMERIC 0 END POLICY END CATEGORY END CATEGORY [strings] category1="Network" category2="Sharing" policyname="AdministrativeShares" DefaultSharesExplain="Enables default workstation administrative shares if enabled or disables if disabled"
You can also download the above adm policy as a text file here. (right click save as)
 Create a new GPO and right click on administrative templates, add administrative template you just created.
Create a new GPO and right click on administrative templates, add administrative template you just created.
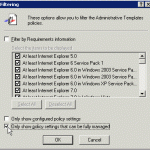
Click machine administrative templates, go into view filtering, unselect/uncheck “Only show policy settings that can be fully managed” the setting is shown in the top picture. Basicly this allows the GPO Editor to show settings, that is not within the default area of registry “preferences” – like ours. Any settings done outside “preferences” will persist if the policy is removed, unlike standard policies.
Open Administrative templates – Network – Sharing
Enable or disable administrative shares.
Done. Might be possible to do this easier, but my google results havent found it 🙂 feel free to add information.
Actually, this is perfectly do-able in GP Preferences–there is an option to remove all administrative or non-admin shares from target systems.
[…] to blog about some useful features in GP Preferences that often slip through the cracks. I saw a blog post today about how you could use a custom ADM file to remove administrative shares on Windows systems. […]
Hi Darren,
Excellent information, Group Policy Preferences definately is nice when it is possible to use it.
Unfortunately it is not always possible to update old clients to work with Group Policy Preferences, however if You are looking at this post and have access to GP Preferences I would recommend taking a look at Darrens blog post about how to use that here http://sdmsoftware.com/blog/2010/06/22/controlling-shares-on-windows-systems/
For the customer I used this specific example, they have some 25.000 workstations controlled by multiple sub-organizations who all independantly decide when and how to upgrade their machines.
i am getting below error while adding ADM template in Administrative templates.
—————————
Administrative Templates
—————————
The following error occurred in \\abc.com\SysVol\abc.com\Policies\{1408E725-2D8C-489A-80C3-696679141481}\Adm\adminshares.adm on line 2:
Error 51 Unexpected keyword
Found:
Expected: CLASS, CATEGORY, [strings]
The file can not be loaded.
—————————
OK
—————————
can i get code in .adm format ? in single file ?
Hi Abdul,
I have added the policy as a txt file in the article, this should help you 🙂
thanks- it worked 🙂
its working perfect- but it disables other shares as well…. like admin$ IPC$….. these share are required for remote installations…etc…..
i just want to disable the access on drives…like C$…etc
is there any way to disable drives only and keep other shares (Admin$/IPC$) alive… ?
thanks in advance….
Administrative shares include all administrative shares, its all or nothing.
I imported all correctly but under network>sharing I can’t show the policyname Can you help me?
I am sorry but not much I can do from here. Would need to look at the code/files, know server language, versions etc. Perhaps take a look at some of your regular ADM files that works, and compare to yours to see what looks different?
Ivan – Check your filtering options. Uncheck the options Only show configured policy settings and only show policy settings that can fully be managed.
please help, created but not updated the policy.
I am sorry but I do not know what created but not updated Means?