Posts Tagged ‘AD’
Active Directory Shadow Group Script – will let you spend less time on updating group memberships
 Introduction
Introduction
If you are just looking for a free shadow group script, either click here for a nice simple one or go to the bottom of this post for the full AD administrated script.
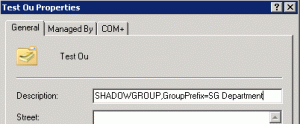
I was looking into Shadow Groups, inspired by a customer migrating from Novell to Active Directory. Apparently in Novell you can use Organizational Units as security groups, and by just moving a user to another OU when they change departments, they will automatically update their security permissions given by their department OU placement.
So what is so great about shadow groups you might ask. Simply put if you have OU’s for departments, where you place users depending on department membership, shadow groups, will shadow the members of the OU in the security group, I assume that is where the name shadow group comes from. This allows you to setup security permissions for a group that is linked to an organizational unit. So when you move user A from department sales, into department accounting, the user A will automatically be removed from the sales security group and added to the accounting security group, effectively updating user A’s permissions automatically. Saves time for large organizations, now a user moving OU does not need to have his groups manually updated.
The first hit on google was a blog post by John Policelli (MVP) explaining shadow groups is not a new type of group in Active Directory, it is rather a concept, when you automatically update the members of a security group from the objects placed in an Organizational Unit. Also he points out that this automatic synchronization is not an existing feature in Windows Server, we need to add it our self. The example he uses with dsquery, dsget and dsmod, works if you manually set it in a script for each OU/Group, I was looking for something easier to manage, that preferably did not require editing of the script that needed to run. I strongly believe scripts that can be maintained from Active Directory will always have a longer life time, since less updates and potential errors happen in the script.
After some more searching I found an article by Jakob H. Heidelberg (MVP and fellow Dane) this one also had a good explanation about what Shadow Groups are and also a download link to a simple VBScript to populate a group with the users in an Organizational Unit. If You are looking for a script to feed the OU and Group and then update the group from the users of the OU, that script will do you just fine and I would recommend you take a look at the article and script he wrote, as it is simpler and less prone to errors by being simple.
My idea of a Shadow Group Script Read the rest of this entry »
How to configure your virtual Domain Controllers and avoid simple mistakes with resulting big problems
So You went ahead and used virtualized Domain Controllers for Your Active Directory domain, congratulations! I am sure You will be happy with the decission, as long as You have a decent virtualizing environment, this will give You both peace of mind, faster recovery and cheaper redundancy.
There is however some special considerations You must do, when You are using virtual Domain Controllers, not to mention, please with sugar on top, ![]() do NOT P2V/Convert Your physical Domain Controllers to virtual, without at least reading this article!
do NOT P2V/Convert Your physical Domain Controllers to virtual, without at least reading this article!
What areas do we need to consider on a virtual DC?
- Time synchronization
- Disk cache
- Suspend/pausing virtual machine
- Snapshots and System State backups
- Performance
Personally I much prefer virtual Domain Controllers, from having a lot of physical ones, but there are some considerations to be made, about perhaps leaving some physical and what features to use on the virtual and what settings to use as well. This article attempts to uncover some of the points to consider, specifically for virtal DC’s. The list is in no way meant to be the only considerations, but is mostly the things that I personally have noticed forgotten in environments I have encountered. Add Your own preferences and research to this and You should be well on Your way to live happily forever with Your virtual DC’s.
How to disable administrative shares on workstations thru Group Policy and avoid spending time on pesty virus infections
 Large companies sometimes have problems with a virus that realy loves administrative shares on other workstations (i.e. c$ and admin$), it will try and break into theese to spread it self directly. The easy option ofcourse being kill the virus or even better harden administrative users and not use administrator rights for normal users! But untill that is an easy, non-political and not so time consuming task, why not disable the administrative shares on the workstations alltogether?
Large companies sometimes have problems with a virus that realy loves administrative shares on other workstations (i.e. c$ and admin$), it will try and break into theese to spread it self directly. The easy option ofcourse being kill the virus or even better harden administrative users and not use administrator rights for normal users! But untill that is an easy, non-political and not so time consuming task, why not disable the administrative shares on the workstations alltogether?
Seems like a perfect thing to do with Group Policy, unfortunately the setting is non-existing default in Group Policies, so by finding the registry key we need to change, a small custom administrative template will do the trick. This could also be used for other registry changes needed with group policy.
We might also want the option to easily enable the administrative shares later, might be used by applications, services, automated installations, etc. Heres is how to do it quick and easy. Read the rest of this entry »
Virtualizing Your Domain Controllers without getting fired!
Please pretty please do not just hit the button and P2V/ColdClone/HotClone/Copy your Windows Server Domain Controllers, regardless if they run Windows Server 2000/2003/2008 etc.
In best case You accomplish to virtualize your domain controllers, wich You could have done with a few simple steps just as easily with out any danger.
In worst case You render your Domain Controllers useless, create several other problems and hickups in your infrastructure, not limited to complete production halt and at least several hours of pain and horror trying to get everything back and running!
Personally I have nothing against virtual Domain Controllers, usually best practice is not to run all kinds of other software or services on a Domain Controller, plus the need to have multiple Domain Controllers for redundancy will quickly add alot of boxes doing very little. Virtualizing some or all of these Domain Controllers, will put better use of ressources and still keep the box seperate from other services. Dont forget to change time synchronisation settings in the w32time service, vmware tools and ntp servers in the ESX’s, but thats another story.
One of the big problems with doing a clone of a Domain Controller, is that if you get problems, you will not notice them untill it is too late. The domain controller will seem to function and work with clients, but it will actually have stopped replicating with all other domain controllers, because it has detected that it has been copied. The result is an inconsistent domain with client records not being updated, they will slowly stop working depending on what domain controller they get in contact with, untill everything goes dead. If you have then virtualized ALL domain controllers, You will be left with 1-3 months of changes going down the tube together with your damaged Domain Controllers. Dont forget to take a full backup of at least 1 Domain Controller before starting your cloning!
So what happens when things go bad? Read the rest of this entry »
How to place FSMO and Global Catalog roles in Active Directory
During installation of Active Directory on a Windows Server 2000/2003/2008 all FSMO roles will automatically be installed on the first server. But Best Practice dictates to move some of theese Flexible Single Master of Operation (FSMO) roles to seperate servers.
If you only have one domain controller (not recommended), there is nothing to do since all roles must be on this server, but if you have multiple servers you should move some of theese roles on to more servers. It is also important to be aware of what servers are Global Catalog servers, especially if you have more than one domain and even if only one domain, they will be prefered by applications like Exchange server.